Business is everywhere, Security should be too
Prisma Access Partner of the Year 2022

Uniting an insurance leader
Read how Telstra Purple has helped Howden Group Holdings, one of the world’s leading insurance brokers, to improve visibility of its cyber posture across the globe though the development of a unique security framework.
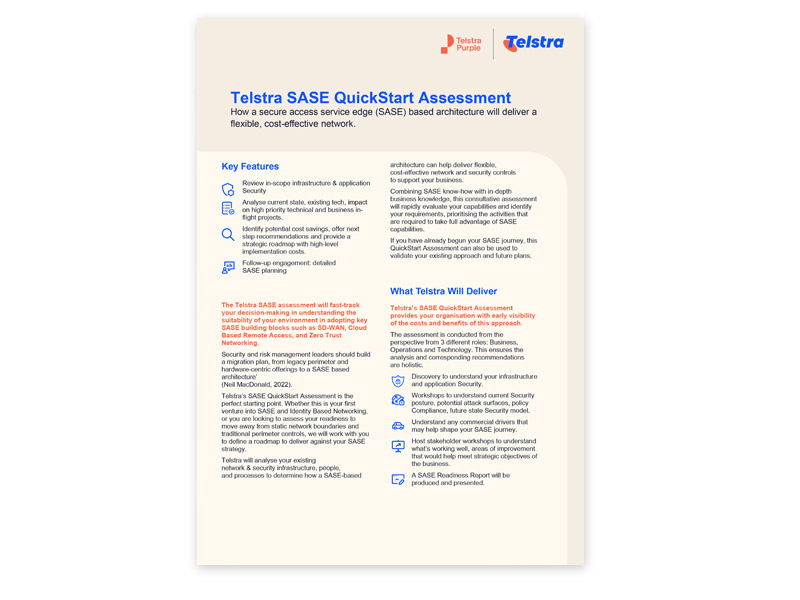
Telstra Purple SASE QuickStart Assessment
The benefits of a SASE based architecture and how it can deliver a flexible, cost effective network.
Already on your SASE journey? The QuickStart Assessment can also assist in validating your existing approach and future plans.

WIFI assessment
Ensure your organisation offers its people an excellent network experience no matter where, and how, they connect with you.

Telstra Security Services
Enable your organisations continued innovation through leading security managed services hosted out of Telstra’s London Hosting Centre.

ClubCISO Information Security Maturity report
This latest report from ClubCISO, a Telstra Purple community, provides an overview of the challenges facing today’s CISOs. Learn more about the factors impacting CISOs’ performance and the hot topics on their radars.
What we do
Telstra Purple has a proven approach that includes security strategy and assessment along with deployment – giving you clear visibility of your business and any potential risks along the way. Our time-tested 4D Methodology enables us to help shape the future of your security posture and we don’t believe in delivering a service and then disappearing. We are constantly there on your journey to offer advice, support, and guidance – as standard. Even if you still want to run your own in-house security operations, we can give the tailored support you need.
How we do it
By engaging Telstra Purple, you benefit from our highly experienced people and the full weight of our expertise. Our experts work as an extension of your team, guiding you through a security and privacy awareness training that’s as unique as you are. We map our recommendations to the security lifecycle of your organisation so you can get the right solution to fit your changing needs, even in an ever-changing digital landscape. The end result? An end-to-end security solution that grows as your business does.
Our Security Advisory and Management Services
Security and Threat Assessment
Our Security and Threat Assessment (SATA) leverages a robust methodological approach to understand your organisation’s current security vulnerability state and risk profile.
Security Target Operating Model
Our Security Target Operating Model (TOM) service aligns your business goals with security objectives and provides a blueprint for security transformation.
Virtual CISO Service
Our VCiso service provides on-demand access to top-flight security professionals who can provide advice and assistance whenever required.
Telstra Security Services
Telstra Security Services jumpstarts your security journey by reviewing your current security posture and mapping services to the security lifecycle of your organisation.

Join our ClubCISO community
Join our private members forum consisting of over 350 global information security leaders. ClubCISO provides a community for security leaders to build their network, be involved in proactive discussion, solve problems and create practical guidance that moves the industry forward.